DEF CON CTF Qualifier 2019 - cant_even_unplug_it
Posted by Klaus Eisentraut in ctf
On Saturday afternoon, I tried a few challenges of the DEF CON CTF Qualifiers. I only was curious and took a quick look, I didn't expect to solve an actual challenge at all. However, one of it was so easy that I solved it almost immediately. Please note, that - despite the date of 2019-05-12 - this blog post was only put online after the end of the challenge!
The challenge
The challenge looked like the following:
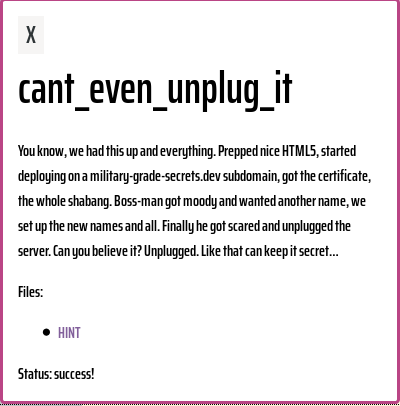
There was an additional HINT file with the following text in it: Hint: these are HTTPS sites. Who is publicly and transparently logging the info you need? Just in case: all info is freely accessible, no subscriptions are necessary. The names cannot really be guessed.
The solution
Immediately after reading this, I knew that I would have to look into the certificate transparency logs. The part of the challenge "got the certificate" gave a big hint. Nowadays, every certificate authority has to follow the rules which the CA/Browser Forum sets. If the certificate authority doesn't follow those rules (which include submitting all certificates they have signed to the certificate transparency logs), then the certificate authority will not be included into major browsers like Google Chrome or Firefox.
So all I had to do was to look for certificates like %.military-grade-secrets.dev on crt.sh.
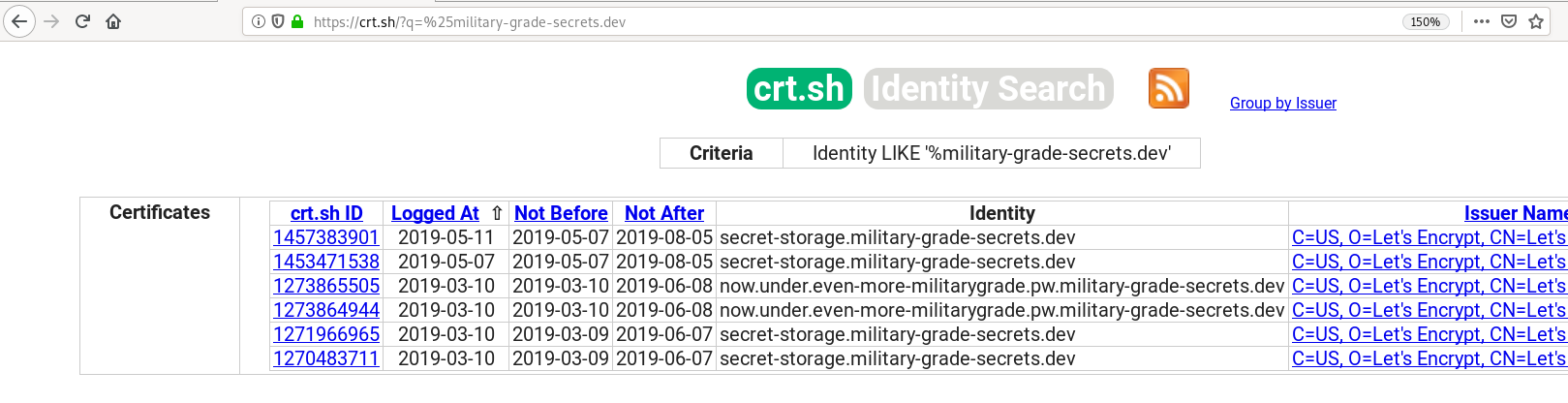
Now, we knew the hostnames of the secret storage, but there was no content any more, just a redirection:
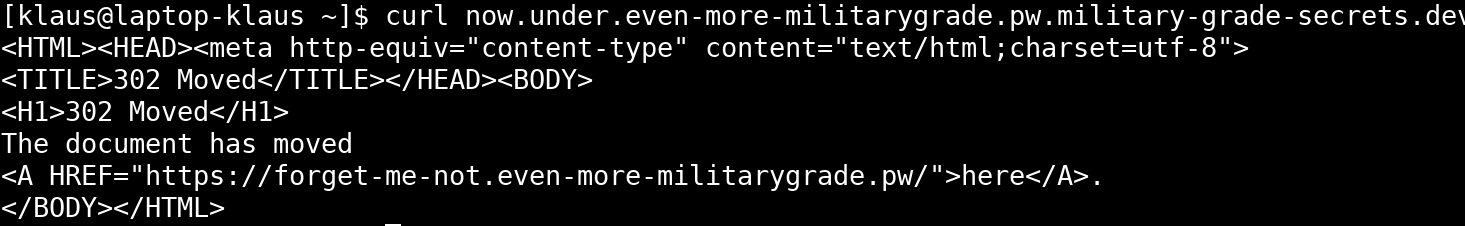
Then I did a full TCP portscan of every host and IP address I had so far. However, only port 443 was open and I ended up with the following DNS names and IP addresses:
secret-storage.military-grade-secrets.dev is an alias for ghs.googlehosted.com.
ghs.googlehosted.com has address 172.217.22.115
ghs.googlehosted.com has IPv6 address 2a00:1450:4001:81d::2013
now.under.even-more-militarygrade.pw.military-grade-secrets.dev is an alias for ghs.googlehosted.com.
ghs.googlehosted.com has address 172.217.22.115
ghs.googlehosted.com has IPv6 address 2a00:1450:4001:81d::2013
forget-me-not.even-more-militarygrade.pw has address 206.189.162.22
For each of the IP addresses above, I tried accessing it without a Host HTTP header and with Host: ... headers according to the names I had already.
I included non-resolving hosts like Host: even-more-militarygrade.pw, too.
However, this lead to nowhere.
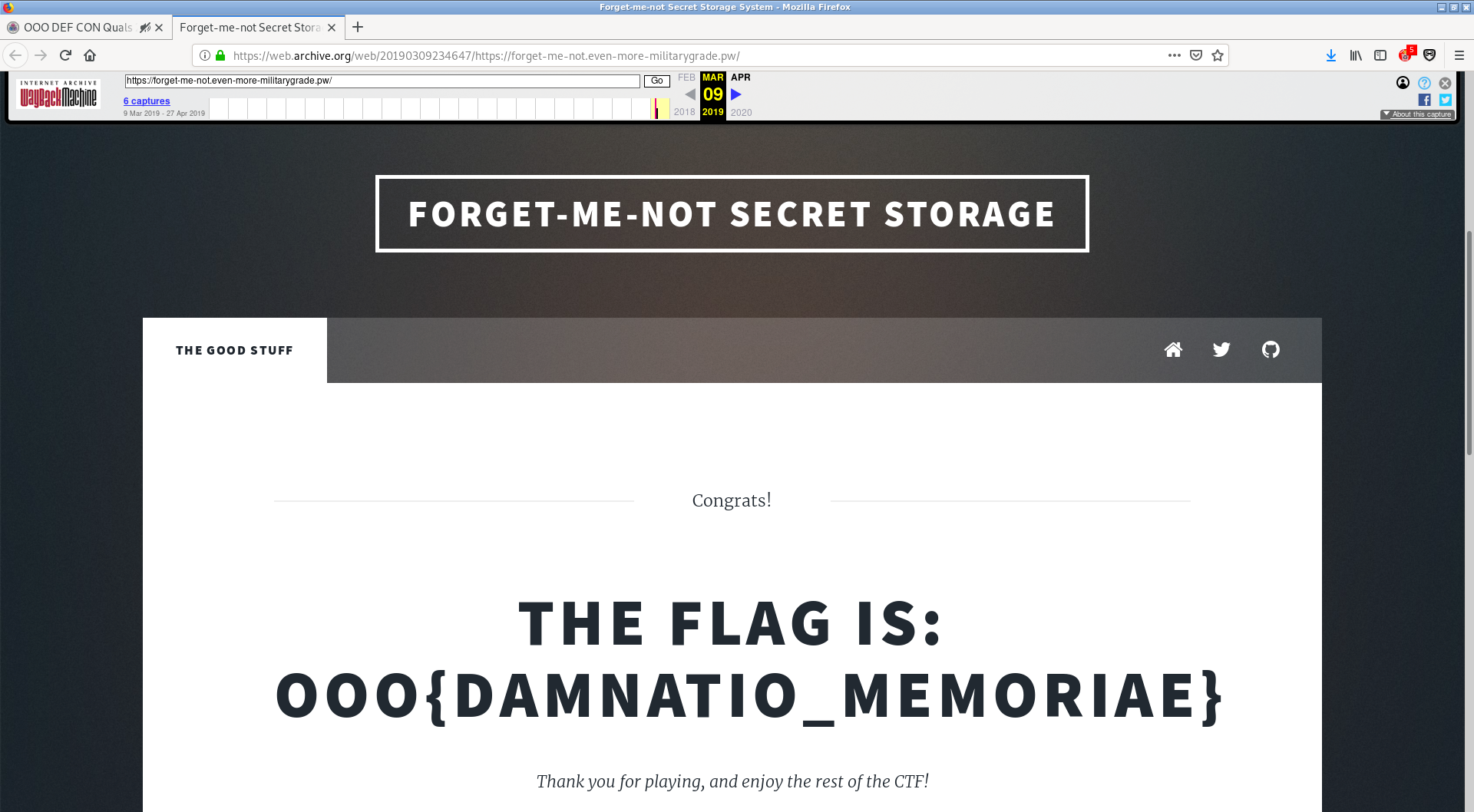
After a short amount of time, I had the idea that the content of those pages could have been archived. Therefore I took a look at the Wayback Machine and it had made snapshots!
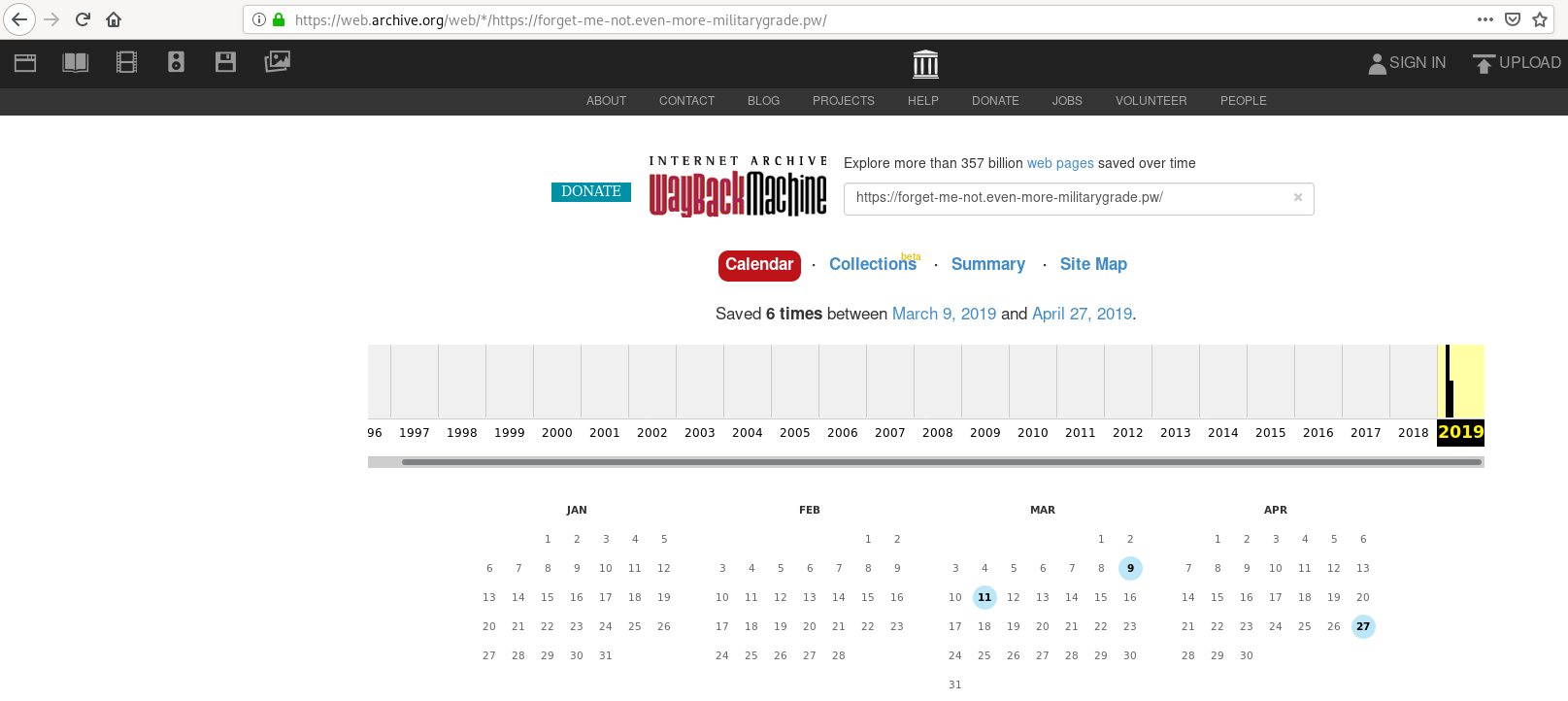
And voila, we found the flag which was OOO{DAMNATIO_MEMORIAE}.